Making KeePassXC great again
Its always been great.KeePassXC is an absolute unit of a password manager.
It's OSS (based), free, secure, has TOTP, cross-platform, CLI and GUI, and it's overall freaking amazing.
For the uninitiated, it's 10x better than saving your passwords in a
.txt file, or god forbid, in a .docx file.
Please, don't do that.
 Look at it, beautiful
Look at it, beautiful
Contents
- Why KeePassXC?
- How to use KeePassXC
- Security best practices
Why KeePassXC?
I've been using it for a while now, and I can't recommend it enough.
Let's start off with the basics as previously mentioned:
- It's free.
- It's open source.
- It's cross-platform.
- It's secure.
- It has TOTP.
And now, let's go a bit deeper.
🗽 Free and Open Source
Free as in freedom, and as in free beer.
You can check their source at GitHub, and in short it's GPLv2 or GPLv3 licensed.
⚖️ Addendum: What is GPL?
GPL (General Public License) is a copyleft license. With it you can:
- Use the software for any purpose.
- Study how the software works and change it.
- Redistribute copies.
- Distribute modified versions.
But you must:
- Make the source code available.
- License changes under GPL.
That's the gist of it.
Why this is important?
Well, you don't want to use a password manager that you can't trust, right?
When you're using proprietary software, you're trusting the company that made it. But as soon you open WireShark and see your passwords being sent to China, you're screwed.
You can just hope that the company is doing the right thing. But with OSS, you don't have to hope.
With the source code available, you can check it yourself, or trust the community to do so.
Leave the hard work to the experts, and profit from it. Simple as.
Nothing against my Chinese overlords, it's just a hyperbolical example.📲 Cross-platform
It's officially supported on Windows, macOS and Linux. You can find details on their official website, but there's also ports for other systems.
Some of them are:
🐧 Addendum: For lazy Linux users like myself
You can install them directly from your package manager, like so:
# Debian-based
sudo apt install keepassxc
# Arch-based
sudo pacman -S keepassxc
# Fedora-based
sudo dnf install keepassxc
# Gentoo-based
sudo emerge -av keepassxc
# OpenSUSE-based
sudo zypper install keepassxc
# Void-based
sudo xbps-install -S keepassxc
# Alpine-based
sudo apk add keepassxc
# NixOS-based
nix-env -iA nixos.keepassxc
🔒 Security
At the end of the day, the most important thing about a password manager is its security.
How secure is KeePassXC? Very.
You see, it uses two key derivation algorithms to encrypt/hash your passwords:
- AES-KDF (Advanced Encryption Standard - Key Derivation Function, 2001).
- Argon2 (Key Derivation Function, 2015).
So there's around 4 types of encrypted databases offered:
- KDBX 3.1 (AES-KDF).
- KDBX 4.0 (AES-KDF).
- KDBX 4.0 (Argon2d).
- KDBX 4.0 (Argon2id).
Since AES-KDF is only CPU heavy against brute force, the best choice is Argon2.
Argon2 is both CPU and memory heavy, it's way more prepared against GPU attacks.
And there's 3 types of encryption algorithms offered for the databases:
- AES (Advanced Encryption Standard, 2001).
- Twofish (Block Cipher, 1998).
- ChaCha20 (Stream Cipher, 2008).
Each of them act differently, but they're all secure.
If you're personally paranoid, here's a tip:
- AES is the most stable, wildly used and analyzed, recommended by the NSA.
- Twofish is the most secure against certain cryptanalysis, but it's way slower.
- ChaCha20 is the most modern, and it's the fastest of them all.
🕗 TOTP
TOTP (Time-based One-Time Password) is a way to secure your accounts with a second factor.
You can use it with your phone, with an app like Google Authenticator or Authy.
Or you can be the smarter one and use it with KeePassXC. Don't worry, you can still use with your authenticator app.
It's a win-win.
Simple as:
- Copying the key and pasting it in the TOTP field in KeePassXC.
- Then reading the QR code generated by KeePassXC with your authenticator app.
How to use KeePassXC
Well, you just downloaded it from the official website or from your package manager, what now?
You might want to read the official user guide, but I'll guide you through the basics quickly.
Boot it up, and let's start fresh.
📦 Starting fresh
After starting up, you'll be greeted with a welcome screen.
 Fresh and clean
Fresh and clean
In here there's a few options, but we'll go with creating a new database.
Select the Create Database option.
And you'll be met with this:
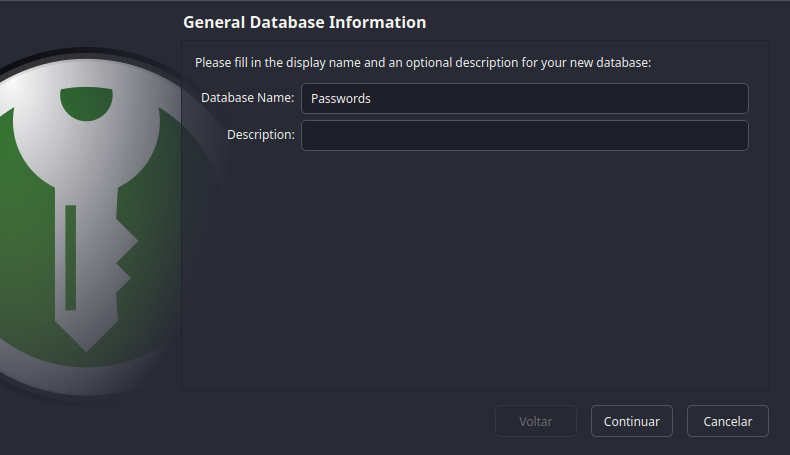 What's your name?
What's your name?
Fill in it's name and details, and click Next.
Next, you'll be met with the Encryption Settings screen.
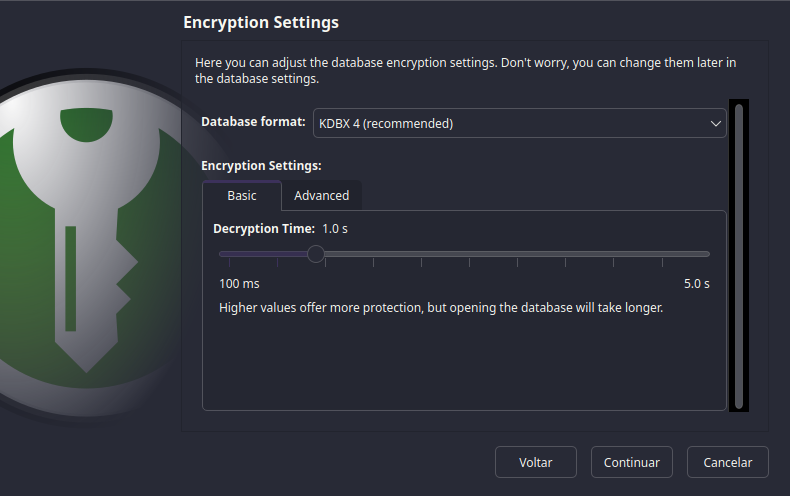 What time do you want
to be, sir?
What time do you want
to be, sir?
This is the most important part of the setup...
So, if you don't understand what's going on, just click Next and live with
the default settings.
If you want to know what's going on, go back to the security section.
And select the options that you feel more comfortable with on the Advanced
tab.
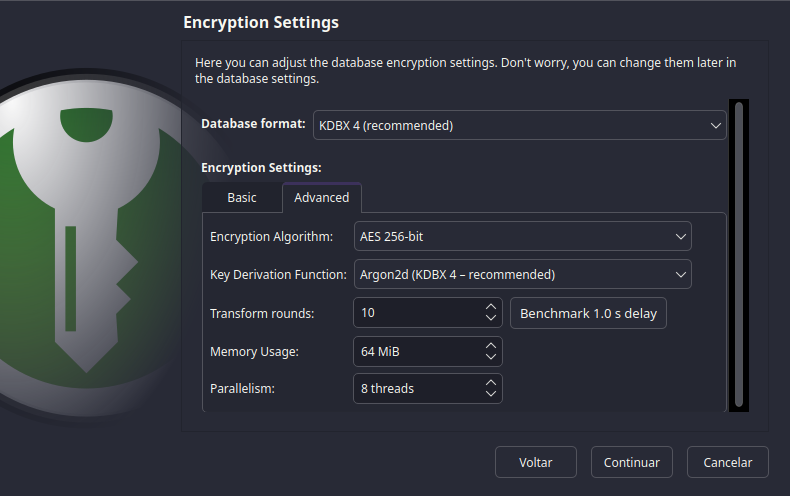 Woa, that's allot
of options
Woa, that's allot
of options
After that, you'll be met with the Database Credentials screen.
In short, this is where you'll create your master password.
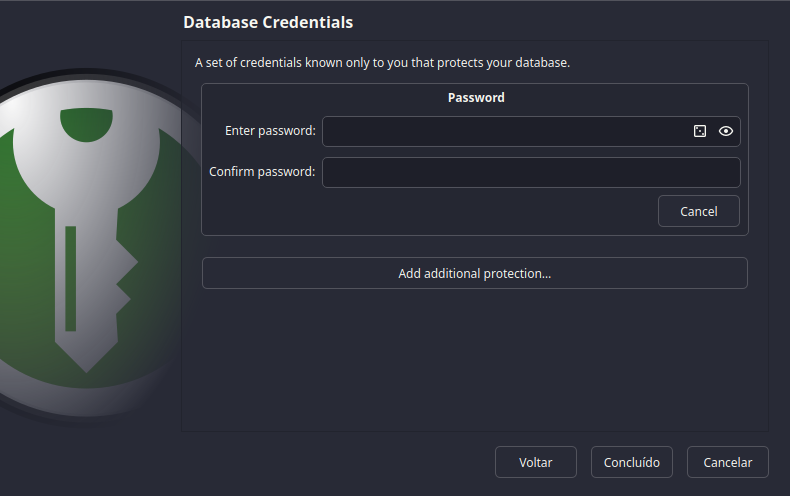 What's the magic
word?
What's the magic
word?
As a rule of thumb, use a strong password.
And DON'T FORGET IT.
My advice is to use a passphrase instead of a password. Like a sentence that you can remember, but it's hard to guess.
It needs to be long, random and unique. From a song, a book, a movie, a game, anything. Not a quote that is well known, but something that you like.
Let's say my password is:
The cake is a lie, but the pie is true.
But I'm really paranoid, so let's salt it with some numbers and special characters:
The cake is a li3, but the pie_is_trué.
You might have noticed that Add additional protection option.
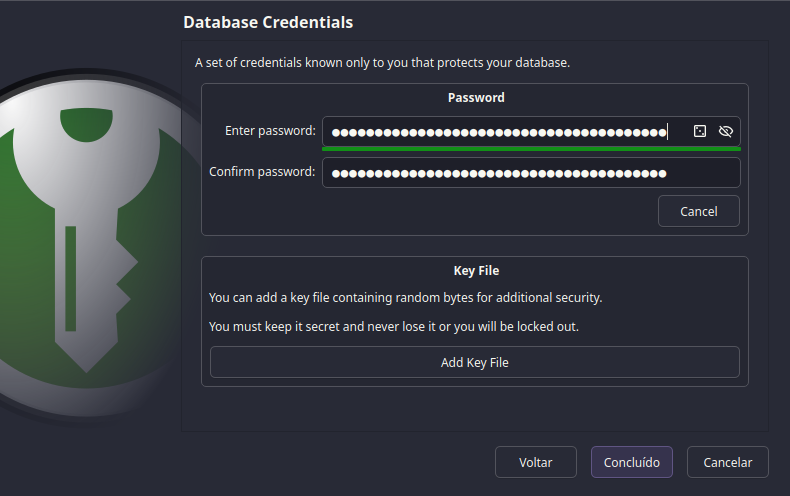 Did you brought
extra protection?
Did you brought
extra protection?
With it you can add a key file to your database.
As the name implies, it's a file that you'll need to open your database. It's way more secure than just a password, but don't lose it.
For the sake of convenience, we'll skip it. The password is enough.
Press Finish and you're done.
Select where you want to save your database, and you're set.
You may want to read the section where to save your database for a better practice.
🗃️ The Database
All set, you're now in the main screen.
If it already feels intuitive to you, feel free to skip this section.
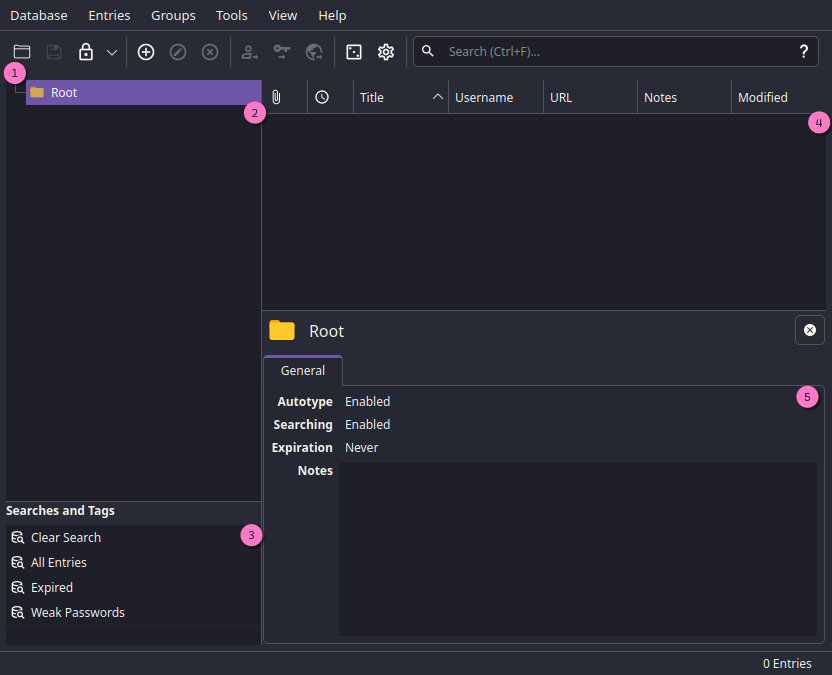 Welcome to the Pleasure Dome
Welcome to the Pleasure Dome
We have the following options:
- Toolbar, from left to right you can:
- Open a database.
- Save the database.
- Lock the database.
- Add a new entry. (Password, Key, File, etc).
- Edit the selected entry.
- Delete the selected entry.
- Copy the selected entry's username.
- Copy the selected entry's password.
- Copy the selected entry's URL.
- Password generator.
- Settings.
- Search.
- Groups, where you can organize your entries in folders.
- Tags, this is a way to organize your entries in a more flexible way.
- Entries, where you can see all your entries in the selected group.
- Entry details, where you can see and edit the selected entry's details.
It's too empty... Let's add a new entry.
📝 Adding a new entry
Right on Add a new entry, CTRL + N shortcut, you'll be met with this:
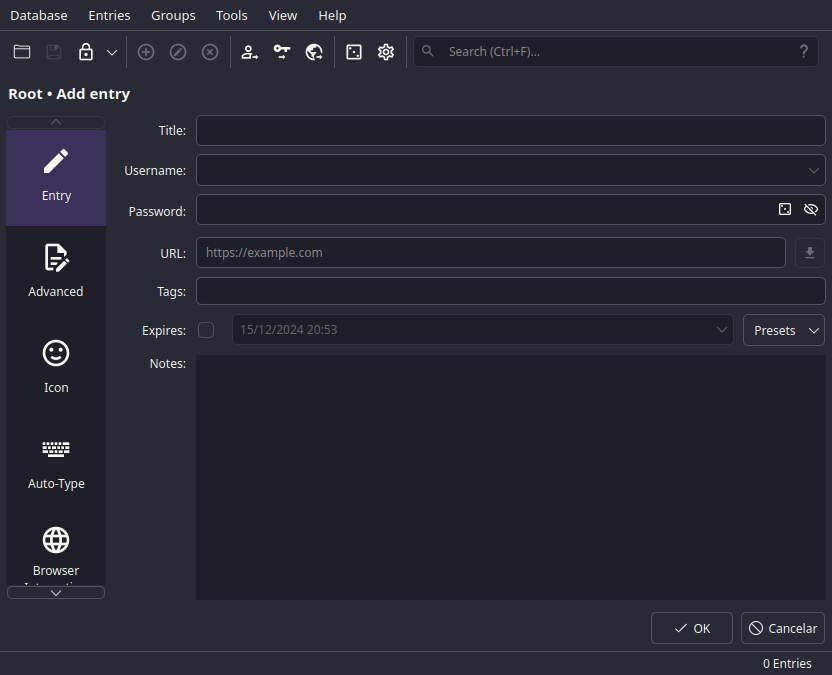 Shh, it's a secret
Shh, it's a secret
Fill in all the necessary details, as such:
- Title, the name of the entry.
- Username, your username or email.
- Password, your password.
- URL, the website's login page URL.
- Tags, to organize your entries, like "game", "work", "microsoft", etc.
- Expires, if you want to set an expiration date for the entry (good practice for business accounts, where passwords need to be changed every X days).
- Notes, any additional information you want to add.
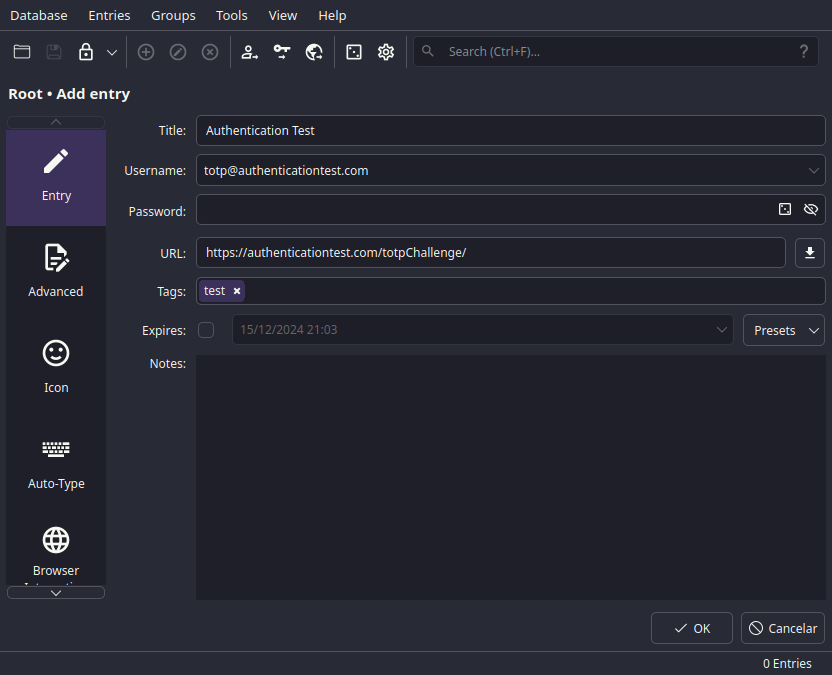 Excellent
Excellent
With the Password field, you can either:
- Generate a new password.
- Type your own password.
It's best to generate a new password, unless you have a good one in mind.
Do not reuse passwords, and do not use weak passwords. No need to worry about forgetting them, you have KeePassXC for that.
I once had my account compromised — one of many affected by Archive.org's breach. I found myself changing passwords across multiple websites at 02:00 AM.
You don't want to be that guy.
🎲 Password generator
When you want to generate a new password, you can click on the Password generator icon.
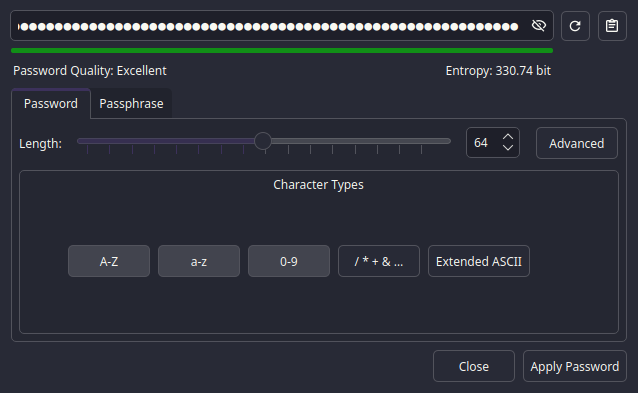 L33t
L33t
Let's not dwell on it's beauty, and let's focus on the options.
About the password length, it's best to use the maximum length allowed by the website.
But, generally it's about 16 to 64 characters.
Now, the character sets.
Oh, the character sets.
You probably will just use 4 of them. Yeah, the Lowercase, Uppercase,
Digits and Special characters.
But if you're creating a password in which will be used by an API, you might
not use Special characters.
It can be a pain to set them to work flawlessly on Environment Variables or URLs, so just make them longer.
Check the Expires option if you're using in API, and change it every 90 days. Better safe than sorry.But there's another option that you might want to use, the Passphrase option.
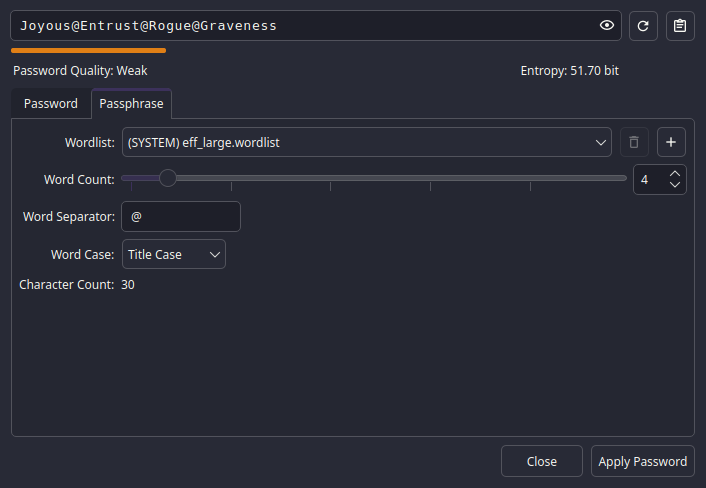
Different from the Password option, the Passphrase option generates a
sentence.
While I don't recommend using it, it's easier to remember.
But it's also easier to guess.
You can also use wordlists like RockYou to generate a password that is way easier to guess.
But that's up to you.
Now, you're done, the password looks safe, and you're ready to save it.
First, click on the clipboard icon to copy the password.
Use it, test it, see if it works.
Then click on Apply Password to save it.
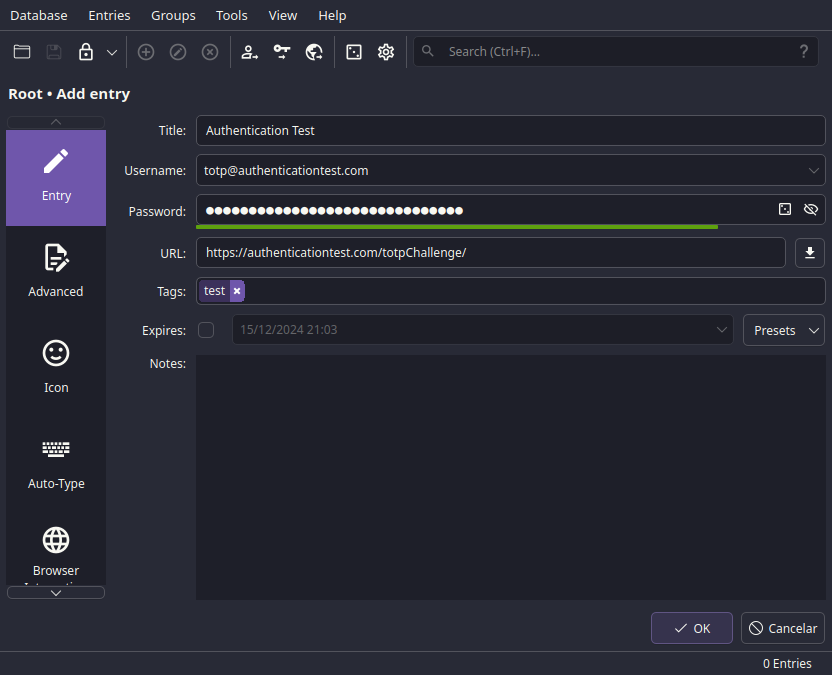
ℹ️ More Entry Details
If you select the Advanced vertical tab, you'll see this beauty:
 The more you know
The more you know
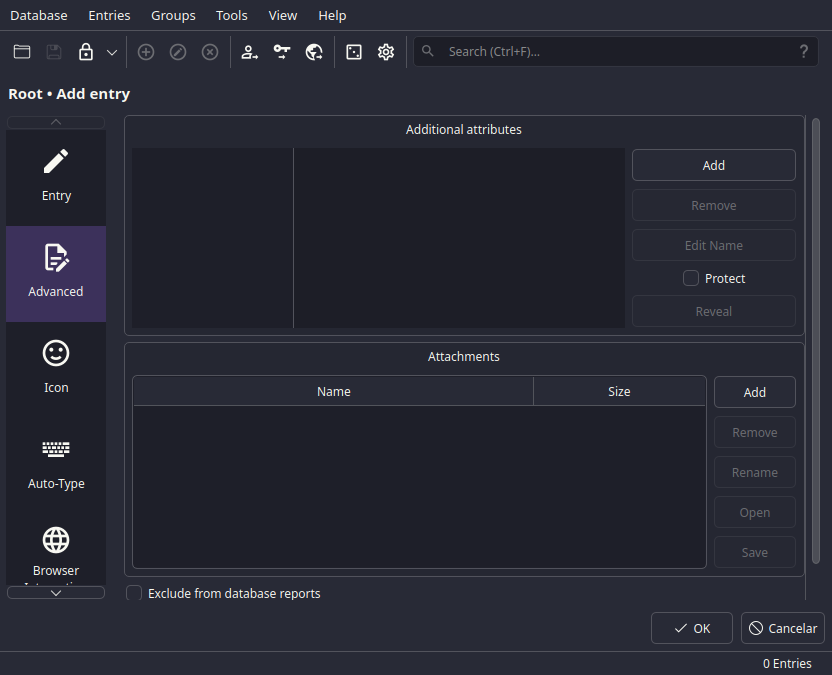
These, my friend, are the Advanced options.
With this, you'll bloat your file with GBs of data, but it's damn useful data.
You can add:
- Custom fields, like "PIN", "Security Question", "Security Answer", etc.
- Attachments, like photos, documents, keys, etc.
Keep them in mind next time you need to fill in the ID field on that Swiss bank account.
Bellow the Advanced tab, there's the Icon tab.
Not too much to say about it, just that you can change the entry's icon.
![]() 🤓
🤓
But, bellow it, the tinkering begins.
Welcome, to the Auto-Type tab.
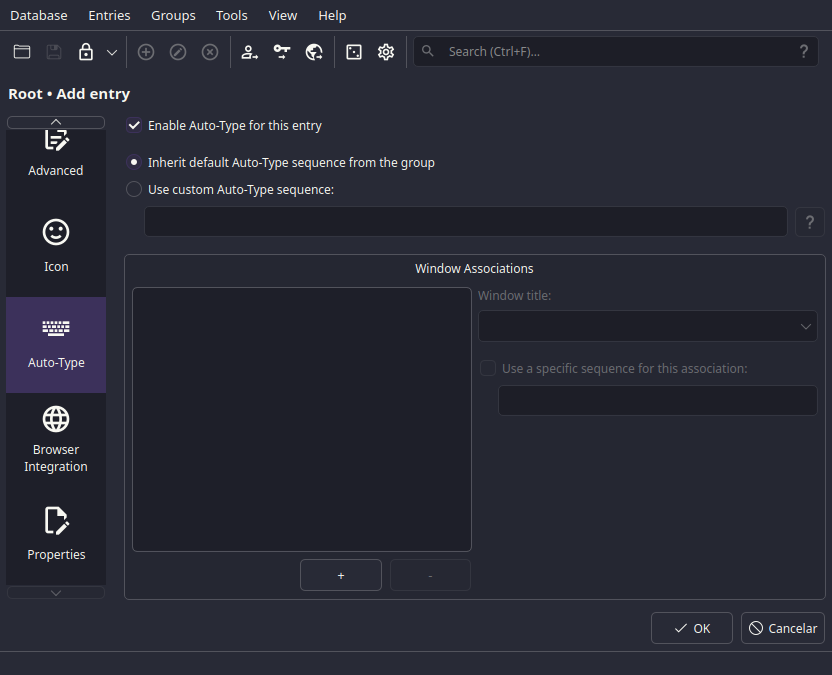 Tinkerer's wet
dream
Tinkerer's wet
dream
It's too complex to explain in a few words, but it can be a powerful automation tool.
I'll try anyways, it's basically:
- You press a hotkey.
- It starts filling a field.
- It types TAB/Enter after finishing it.
- It fills the next field.
- It presses Enter.
- You profit!
You can find a way more in-depth explanation in this adoc here.
The last one in which is useful, is the Browser Integration tab.
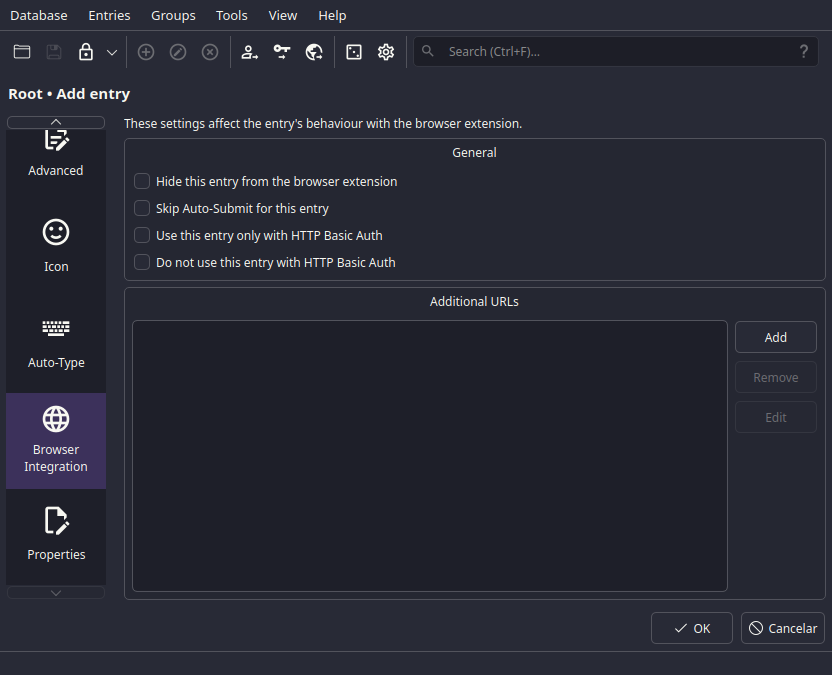 Another one
Another one
Here it lets you fine-tune the browser integration.
And leave multiple URLs for the same entry.
Effective.
🕗 Setting up the TOTP
Now, let's set up the TOTP.
To do so, you'll need to right-click on the entry, and select TOTP > Set up TOTP.
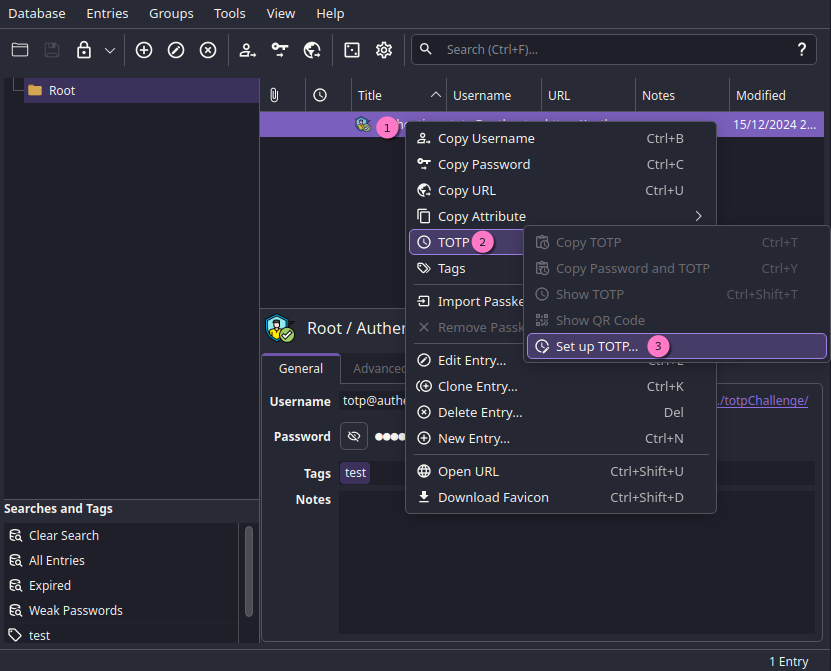
Then, you'll be met with this:
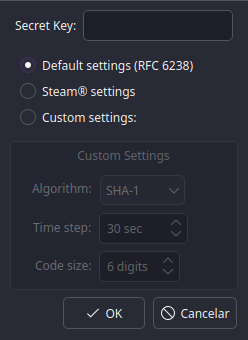
We will need to get the Secret from the website.
I'll be using Authentication
Test for this example. In it we
can find the Secret above the QR code.
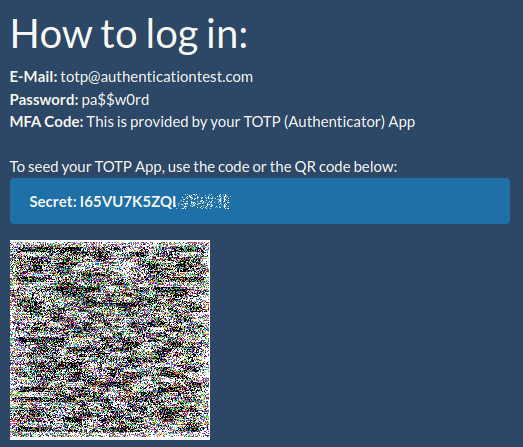
Paste it in the Secret field, and click OK.
Unless the website uses a custom TOTP, it should work out of the box. If not, they'll probably have a guide on how to set it up.
Voilà, you're done.
You now can right-click on the entry, and select TOTP > Copy TOTP.
Or Show TOTP to see the code and the time left, also there's Show QR Code
to scan it with your authenticator app as expressed in here.
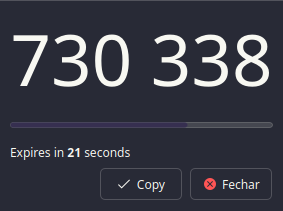 Working
around the clock
Working
around the clock
📥 Importing entries
If you're coming from another password manager, or your password manager is the web browser, you might want to import your entries.
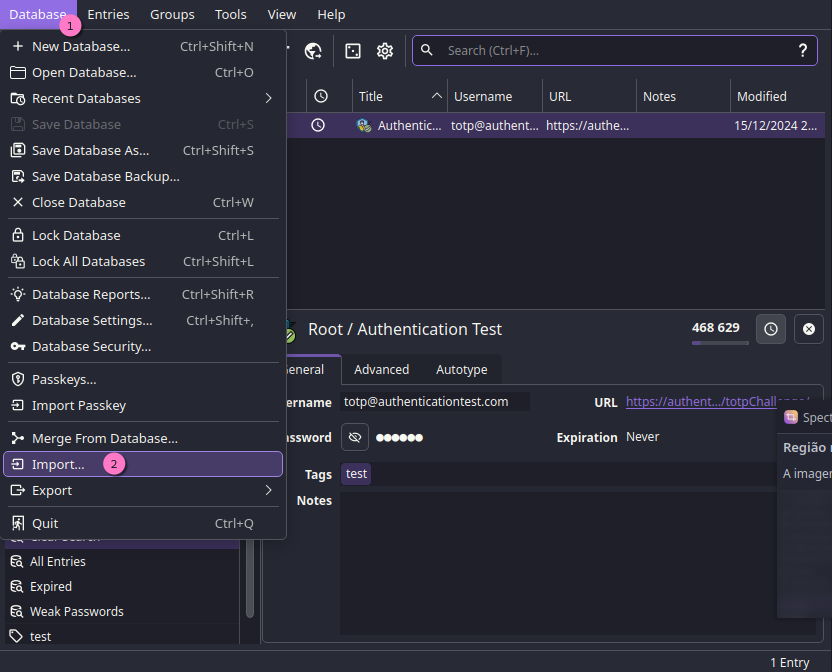 To select the
To select the Import option, just click the Database option on the menu
There's a few options, a couple for the most common password managers, and one
for .csv files.
Each of them have their own way of importing, but it's generally the same. So
we'll be sticking with the .csv file.
🌐 From a web browser
Export your passwords to a .csv file.
These following links is where you can find how to export your passwords from your browser:
Copy and paste them, they're blocked for security reasons.
And then:
- Open the
Importoption; - Select the
.csvoption; - Select the
.csvfile; - Select an
Existing Database; - And
Continue.
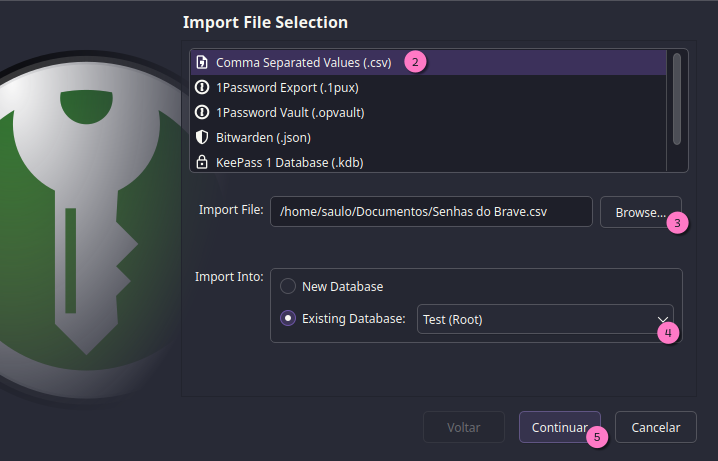 You can also import to a
You can also import to a New Database
Now, look closer at the values. You want to select what each column is
in Column Association.
Then see what changes are made on the Preview frame, and if some values
aren't being imported correctly, fine-tune the Encoding.
 Importing the goods
Importing the goods
After that, just click Finish and you're done.
🔎 Searching
You've filled in your share of entries, but now how do you find reused passwords?
And by the way, how do you find reused emails? Or repeated entries?
The search works with fields which you specify.
| Field | Description |
|---|---|
t |
Title |
u |
Username |
p |
Password |
url |
URL |
n |
Notes |
g |
Group |
attr |
Attributes |
attach |
Attachments |
is:expired |
Expired entries |
is:weak |
Weak passwords |
On the search bar you can use Regex to find what you want.
Things like:
| Search | Description |
|---|---|
^saulo |
Find all entries that start with saulo. |
saulo$ |
Find all entries that end with saulo. |
saulo.*jose |
Find all entries that have saulo and jose in it. |
saulo|jose |
Find all entries that have saulo or jose in it. |
saulo\s+jose |
Find all entries that have saulo and jose with one or more spaces in between. |
And so on.
To use Regex, just tag the field with a * modifier as such:
*u:saulo.*jose.
The above example will find all entries that have saulo and jose
in the Username field.
The possible modifiers are:
| Modifier | Description |
|---|---|
* |
Regex |
! or - |
Not |
+ |
Exact |
Or you can just type out the title without any modifiers. The search bar will do its job.
🌐 Browser Integration
Integration with your browser is a must. There's official extensions for any browser based on:
After installing them, you need to enable and configure KeePassXC to communicate with the browser.
Just open the Browser Integration tab inside the Settings option.
And enable the necessary options.
 The bridge
The bridge
After enabling them, when you next try to connect with the browser, it will ask to name the browser.
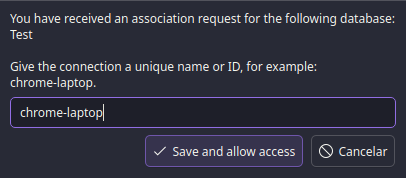
Save it, and you're done. You now have a safe bridge between your browser and KeePassXC.
When you need to fill in a password, query the extension and give the browser access to the entry, and it will fill it in for you.
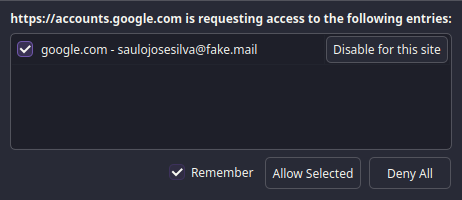
🕵️ Have I been Pwned?
Well, well, well. The (web) world isn't a perfect place.
Sometimes, your passwords are leaked. Doesn't matter how secure your password is, if the website is compromised, your account is compromised.
How can you keep up with it? KeePassXC has your back.
First off, open your Database Reports option.
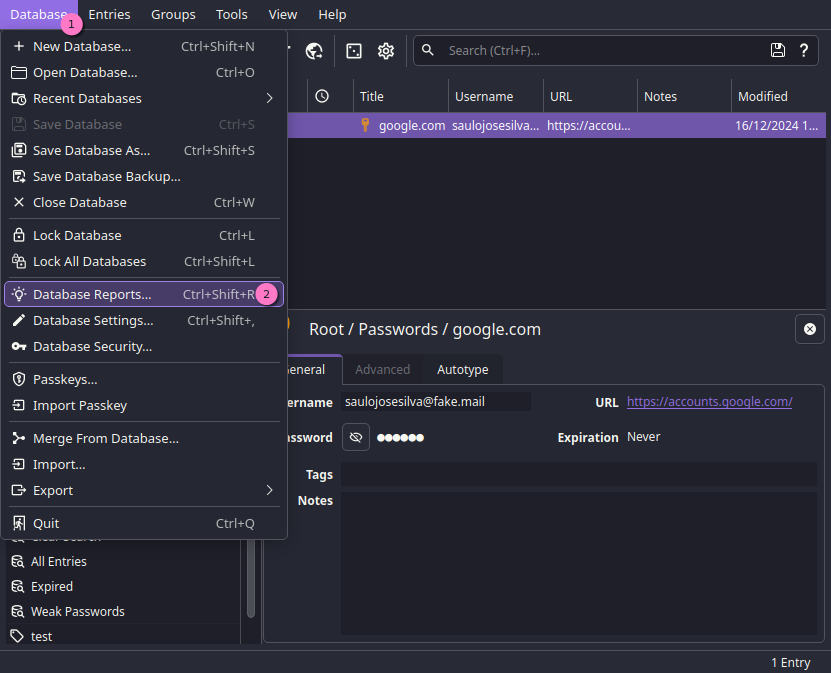
And you'll be met with this window:
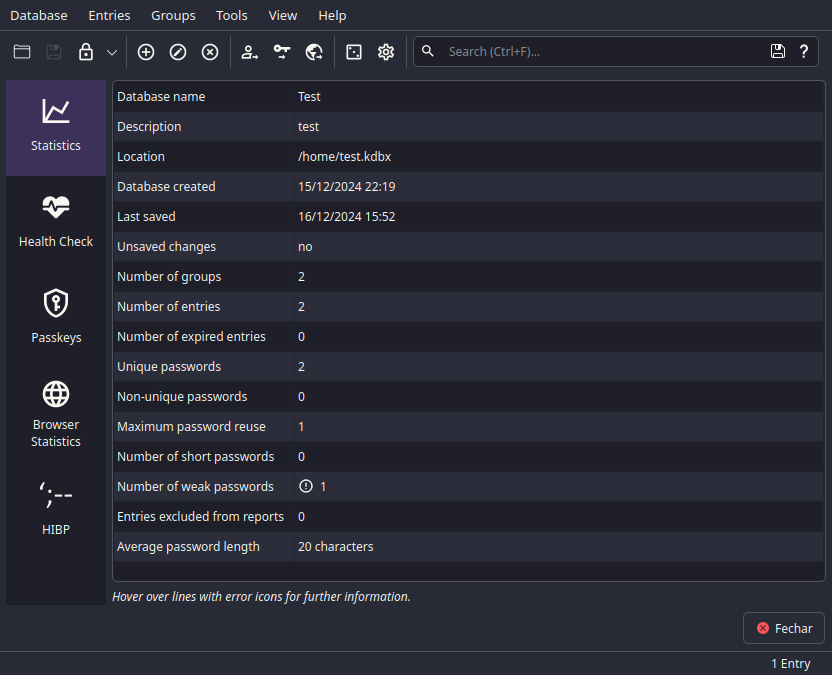 You can use your free time to explore this, might be useful
You can use your free time to explore this, might be useful
In here, you can see a few options, but we'll be focusing on the HIBP tab.
In there you can check if your passwords have been leaked. The warning is that you're sending your IP, and the number of passwords to the HIBP API.
If you're really, and I mean reaaally paranoid, you can opt to not use it.
But after you confirm, you'll be met with this:
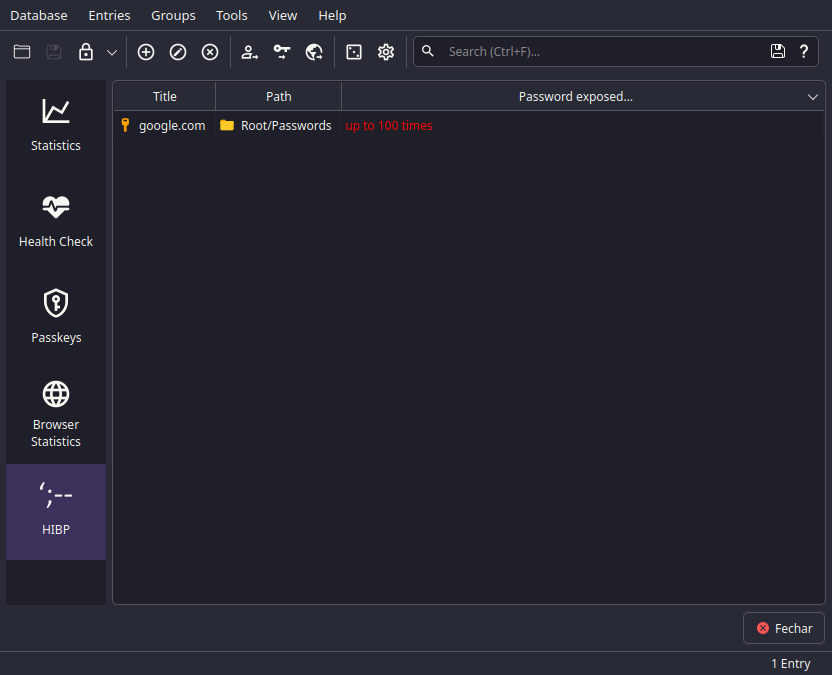 Beat it, the snitch
Beat it, the snitch
And in here it'll list out password hashes that have been leaked in the past.
Ouch, look at that, my 100% secret passwordteste0123 was exposed allot.
Security best practices
As you've might noticed, some tidbits of security practices were mentioned, but let's go a bit deeper.
One thing, I'll separate into 3 sections:
It's best to follow them all, each one is important. But many of them are optional, unless you're being targeted or you're paranoid.
🛡️ Data security
When it comes to data security, you need to be aware of a few risks and disasters:
- Data loss, by natural disasters, hardware failures, or even human error.
- Data theft, by copying, hacking, or even physical theft.
- Compromised security and leaks, by third-party software, or even your own.
- Data corruption, by software bugs, or even failed backups.
We'll tackle them one by one.
🌪️ Data loss and corruption
This is the worst-case scenario, and it's common as well.
There's a lot to consider if you want to be really safe from it.
The golden rule is: DO NOT save the backups in one place only.
One way to prevent it is to have multiple backups: multiple offline devices with limited access, and some online backups.
📦 Offline backups
Here's some bullet points to consider:
- Offline backups should be stored in a safe place, obviously.
- First off, do not burn, or in any way make permanent write on read-only media. But try to keep your backups in read-only permissions, until you need to update them.
- You need to have a reliable storage device, nothing out of the flea market. Like fake SSDs and USBs, use a reputable brand or search for any if in doubt.
- Take caution if you're using a HDD, they're beyond fragile. A bad actor can easily destroy it with a strong magnet without even touching it or connecting it to a computer.
- If you're encrypting your backups, take caution, as it can scramble the KeePassXC database encryption, and you might not be able to recover it.
- Make sure to update your backups regularly, and test them to see if they're working.
🌐 Online backups
Sensitive data should not be stored online, unless you're using a cloud service or a VPS, you need to take some precautions.
- Use a secure service or self-hosted solution, avoid Google Drive, Dropbox, OneDrive, etc.
- Use stable and secure software, like Debian, CentOS, and update them regularly.
- If possible, create multiple containers, or VMs, to separate/divide your data, keeping the root system clean.
- Protect your VPS or cloud service from outside threats, use a firewall (avoid Cloudflare).
👮 Data theft and compromised security
Data theft is often a one-time event with devastating consequences — once it happens, say goodbye your privacy. It's hard to keep tabs on it, but you can prevent it or make the life of the thief harder.
Let's say that your files in Google Drive were compromised, now what?
🛡️ Mitigate the damage
It's done, they've got your files, mission failed, but you can still prevent further damage.
While they can't decrypt your KeePassXC database, you have the upper hand.
- Change your passwords, all of them, and use a password manager to generate new ones.
- Check your accounts, see if there's any unauthorized access, and report it.
- If you kept SSH keys, revoke them, and generate new ones, and check access on
your servers with
fingerorlast. - Credit cards and bank accounts, check for any unauthorized transactions, and ask for a new card.
You can't protect yourself from everything, some attached files inside the database, if the encryption is broken, will be exposed.
If you're being politically targeted, make sure to never ever hint at your KeePassXC database, and use a false backup, or a decoy with invaluable data.
Make sure all of yours backups are well hidden, as if found they might use a rubber hose attack on you, and make sure to use a really random master password instead.
🔌 Protect your offline data
When you're using offline backups, you're exposing yourself to physical threats. So let's be paranoid about it.
- Reboot your systems if you're borrowing your device or using a public one. As RAM can hold sensitive data, and it can be extracted with a cold boot attack.
- Do not leave your backups unattended, keep them in a safe place after usage, locked.
- Social engineer your backups, make sure to name them something inconspicuous,
like
start.bin,musics.rar, etc. - Maybe encrypt them, with LUKS, VeraCrypt, etc. But remember, it can scramble the KeePassXC database encryption.
- Always shred files before deleting them, overwriting them with random data and bits.
Now these two are kinda obnoxious, but they are fun.
- Split your backups, to smaller files and scatter them around. Try to make a puzzle that the thief can't solve.
- As a last resort, use false backups, with fake data like zip bombs or unimportant accounts, to throw off the thief. ¯\_(ツ)_/¯
📡 Protect your online data
When you're using a VPS or cloud service, you're exposing yourself to the world.
- Use guerilla tactics, open all ports to nowhere, and avoid using default ports.
- Do not leave a chance for your ISP, use tunneling protocols like SSH and VPN.
- Block unwanted access, use fail2ban, iptables, ufw, etc. to ban IPs that are trying to access your server.
- Also social engineer your files, make sure to name them something inconspicuous,
like
start.bin,musics.rar, etc. - Do NOT use privacy invading services, they can copy your data and wait until a new crytoanalysis method is found to decrypt it.
🖥️ Device security
Making your device secure is a must, as it's the first line of defense.
Common mistakes include:
- Leaving your device unattended, and unlocked.
- Saving sensitive accounts on your smartphone and laptop.
- Using public Wi-Fi to access sensitive accounts.
- Leaving ports, NFC and Bluetooth open.
- Inserting untrusted USBs.
🚪 Lock your device
When you're not using your device, lock it.
My favorite passwords for PIN are mathematical formulas or sequences, like what's the 18th Fibonacci number?
But the best way is to not have patterns. And use a passphrase instead of a PIN.
Do not use your device password for your KeePassXC database, and vice versa.
📂 Where to save your database
Besides the backups, you need a place to store them for everyday use.
My recommendation is to keep your personal and unimportant database in your personal computer, in a laptop, a USB drive and even on your phone.
For more important databases, keep them in your trusted computer, and don't access these accounts anywhere else.
These important accounts are, but not limited to:
- Your bank account.
- Your servers access.
- Your work accounts.
- Any political or sensitive accounts.
- Personal API keys.
📡 Public Wi-Fi and open ports
When you're using public Wi-Fi with open ports or Bluetooth, you're in for a lot of trouble.
That's why you need to separate your personal and sensitive accounts. And never access them with devices on public areas.
It's even possible to send remote commands to your device by Bluetooth if they're not secured.
💾 Untrusted USBs
It's rather easy to exploit the AutoRun feature on Windows, and even on Linux you can exploit the udev rules, or use a Rubber Ducky with remote code payload.
So, again, that's why you need to separate your personal and sensitive accounts.
Your laptop is your personal device, and your personal USBs are for personal use only.
Not sensitive accounts, not work accounts, etc.
👤 User security
User security is the weakest link in the chain, and that includes you.
This is more about common sense than anything else. But I'll try to give some options.
🔑 Passwords
As I've said before:
- Never reuse passwords.
- Don't use passwords made with dictionary words.
- Do not leave your passwords in plain text.
- Generate random passwords when possible.
And if you need to write them down physically, do not write them in a Post-It and stick it to your monitor.
Instead, do the sensible thing and cypher them, or use an object to signalize parts of the password in a book or in a safely hidden paper.
Also, if you want to check if your password is common, you can check it on the classic RockYou.
💿 Your OS and Environment
While not directly related to the user itself, it's important to take note when you're using your computer with a certain environment:
- Windows is the most targeted OS, and it's the most vulnerable.
- Windows 11 can send data from Screen Capture to Copilot, a big no-no.
- Windows 11 send data from search bar towards their servers.
- Apple has a history of privacy breaches, like flagging your photos for "illegal content".
So, I recommend using a privacy-focused Linux distribution, like Tails for any sensitive work.
But that's the exception, generally if you either use MacOS or Linux, you're good to go if you keep tabs on the services you're using.
And that's it, you're a 'noid KeePassXC user now.
Or you're just prepared for the worst, and that's good too.
I'll keep updating it in the future, but for now, that's all.